Digital Credentials: why context matters

This post was prompted by attending another excellent AMA session with the Digital Credentials Consortium (DCC) yesterday. The discussion raised a recurring issue in the world of digital credentials: unrealistic expectations. People often expect too much and too little from these technologies, leading (I would argue) to both over-ambitious and underwhelming demands.
Overly ambitious expectations
There are many people, who seem to want digital credentials, such as Verifiable Credentials (VCs), to be universally applicable, solving every conceivable use case across different contexts. This mindset is what led to brief craze for blockchain-based credentials, where similar expectations were placed on distributed ledgers to ‘revolutionise’ various industries. A common desire is for these credentials to be “soul-bound,” linking them irrevocably to an individual’s biometric data. While this might sound like an ideal solution for ensuring security and authenticity, it introduces really quite significant privacy concerns. Tying credentials to biometric details could lead to a scenario where every interaction or transaction becomes a potential privacy risk.
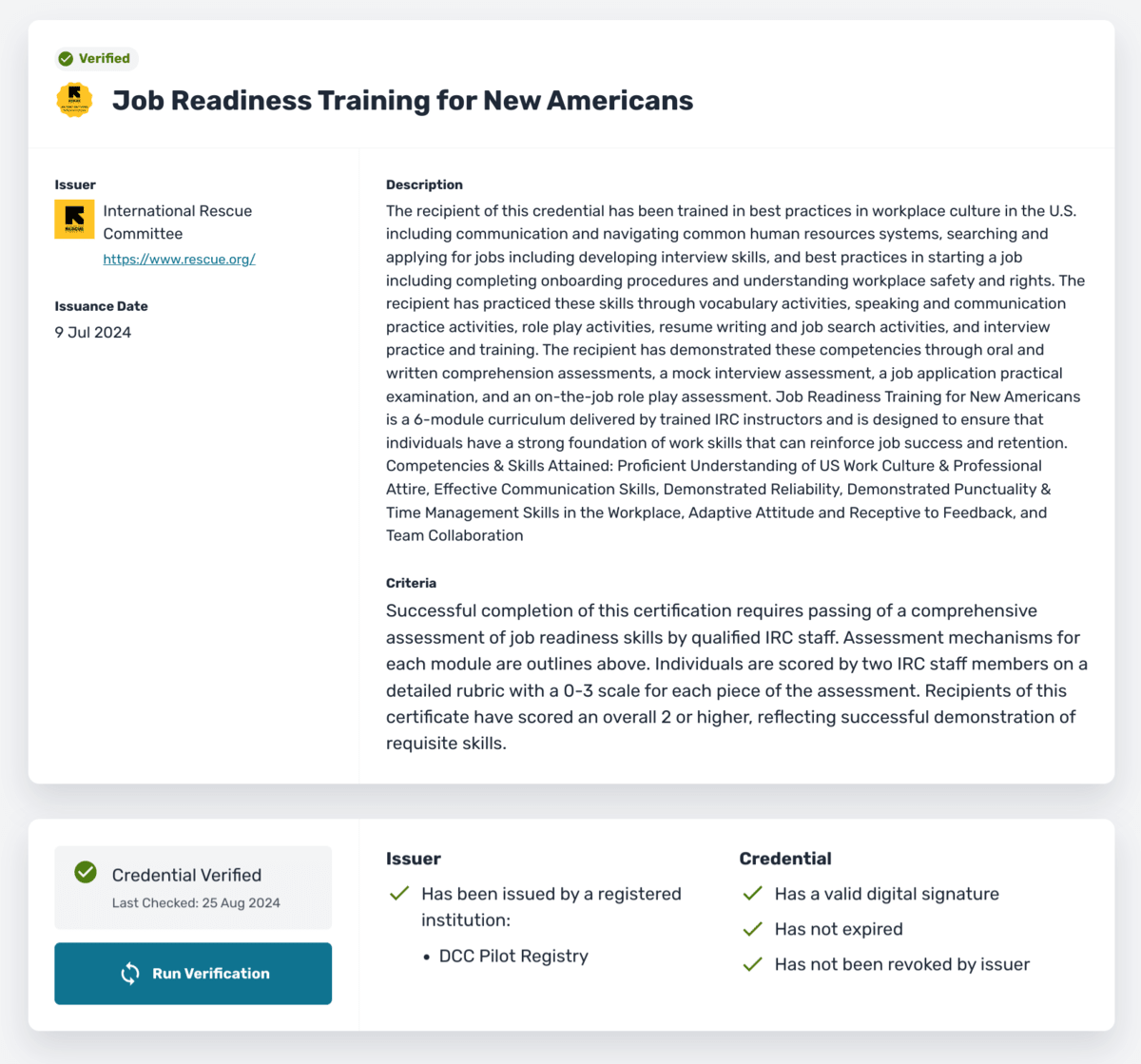
This expectation fails to account for the importance of context in the use of credentials. Even the most critical credentials, such as passports, are context-dependent. Passports are used in specific scenarios—usually, crossing borders—where the context dictates the level of scrutiny and the type of verification required. Translating this into the digital world without considering the context creates unnecessary complexity and risks. Most things are not as critical as passports, so using them as a benchmark doesn’t make much sense.
The importance of context
Credentials are most valuable when they are context-specific. For example, Kerri Lemoie, Director of the DCC, uses the example of proving that you’re of legal drinking age. In this case, it’s unnecessary to disclose your exact birthdate; all that matters is whether you meet the age requirement. This selective disclosure is important, particularly for marginalised communities, such as transgender individuals or refugees, who may need to prove their eligibility or identity without revealing other, potentially sensitive, information.
The challenge here lies in creating digital credentials that respect context while providing the necessary information. It’s not just about what the credential says, but how, when, and where it is used. By designing credentials that allow for selective disclosure, we can protect privacy while ensuring that the credential fulfils its intended purpose.
The evolving nature of digital credentials
Traditional, offline credentials are static: once issued, they don’t change. In contrast, digital credentials offer the potential for evolution. They can be updated, linked to other digital artefacts, and grow in value over time as they gain endorsements or additional evidence.
This dynamism, however, places an unfair burden on credential holders. Employers, for instance, often expect to sift through hundreds or thousands of applications, using credentials as a filtering tool. This approach treats credentials as mere checkboxes, ignoring their potential richness and depth. Instead, there should be a shift towards recognising ‘benchmark’ credentials that indicate a candidate has met the minimum requirements, with further scrutiny placed on unique qualifications or endorsements that set them apart.
Credentials have traditionally been seen as part of wider ‘eportfolios’ but there is less understanding that, these days, credentials can be mini-eportfolios in and of themselves.
The relational aspect of credentials
At their core, all credentials are relational. They represent an attestation from one party to another—a way of saying, “This person did this thing” or “We vouch for this individual.” This relational nature is fundamental to their function, yet it’s often overlooked when people are talking about digital credentials.
The relational aspect becomes even more critical in the digital space. For instance, the concept of ‘trust registries,’ such as the one established by MIT, allows for the verification of credentials without needing to expose the underlying data. Tools like VerifierPlus enable this process, providing a way to check the validity of a credential quickly and efficiently. This is not unlike scanning a passport at a border crossing—simple, effective, and crucial for maintaining trust.
Privacy and security considerations
As digital credentials evolve, privacy concerns should remain at the forefront. It’s critical that credential holders have control over what information they share, and with whom. The current specification for Verifiable Credentials allows for this selective disclosure, but the user experience is still catching up. Some situations may require nothing more than proving control over a credential, while others may necessitate revealing a name or even providing biometric proof.
The key is flexibility. By designing systems that allow for a range of disclosures depending on the context, we can protect privacy while ensuring that credentials remain functional and trustworthy. This requires thoughtful UX design, as the technology must be intuitive and accessible to all users, not just those with technical expertise (as is the case currently).
Conclusion
Digital credentials hold immense potential, but this potential is only realised when we manage expectations, maintain context, and prioritise privacy. By recognising the relational nature of credentials and shifting some of the burden away from credential holders, we can create a more balanced, effective system that respects both individual rights and societal needs.
As we move forward, it’s crucial to keep these considerations in mind, ensuring that digital credentials are not just technically sound, but also socially responsible and practical in their application.
Image: Matej Spulak